Datasheet 搜索 > 微控制器 > Microchip(微芯) > DSPIC30F3013-20I/SP 数据手册 > DSPIC30F3013-20I/SP 用户编程技术手册 5/66 页

 器件3D模型
器件3D模型¥ 43.038
DSPIC30F3013-20I/SP 用户编程技术手册 - Microchip(微芯)
制造商:
Microchip(微芯)
分类:
微控制器
封装:
DIP-28
Pictures:
3D模型
符号图
焊盘图
引脚图
产品图
页面导航:
引脚图在P2Hot
导航目录
DSPIC30F3013-20I/SP数据手册
Page:
of 66 Go
若手册格式错乱,请下载阅览PDF原文件
© 2010 Microchip Technology Inc. DS70102K-page 5
dsPIC30F Flash Programming Specification
5.0 DEVICE PROGRAMMING
5.1 Overview of the Programming
Process
Once the programming executive has been verified
in memory (or loaded if not present), the dsPIC30F can
be programmed using the command set shown in
Table 5-1. A detailed description for each command is
provided in Section 8.0 “Programming Executive
Commands”.
TABLE 5-1: COMMAND SET SUMMARY
Command Description
SCHECK Sanity check
READD Read data EEPROM, Configuration
regi
sters and device ID
READP Read code memory
PROGD Program one row of data EEPROM
and
verify
PROGP Program one row of code memory and
verify
PROGC Program Configuration bits and verify
ERASEB Bulk Erase, or erase by segment
ERASED Erase data EEPROM
ERASEP Erase code memory
QBLANK Query if the code memory and data
EEPROM are blank
QVER Query the software version
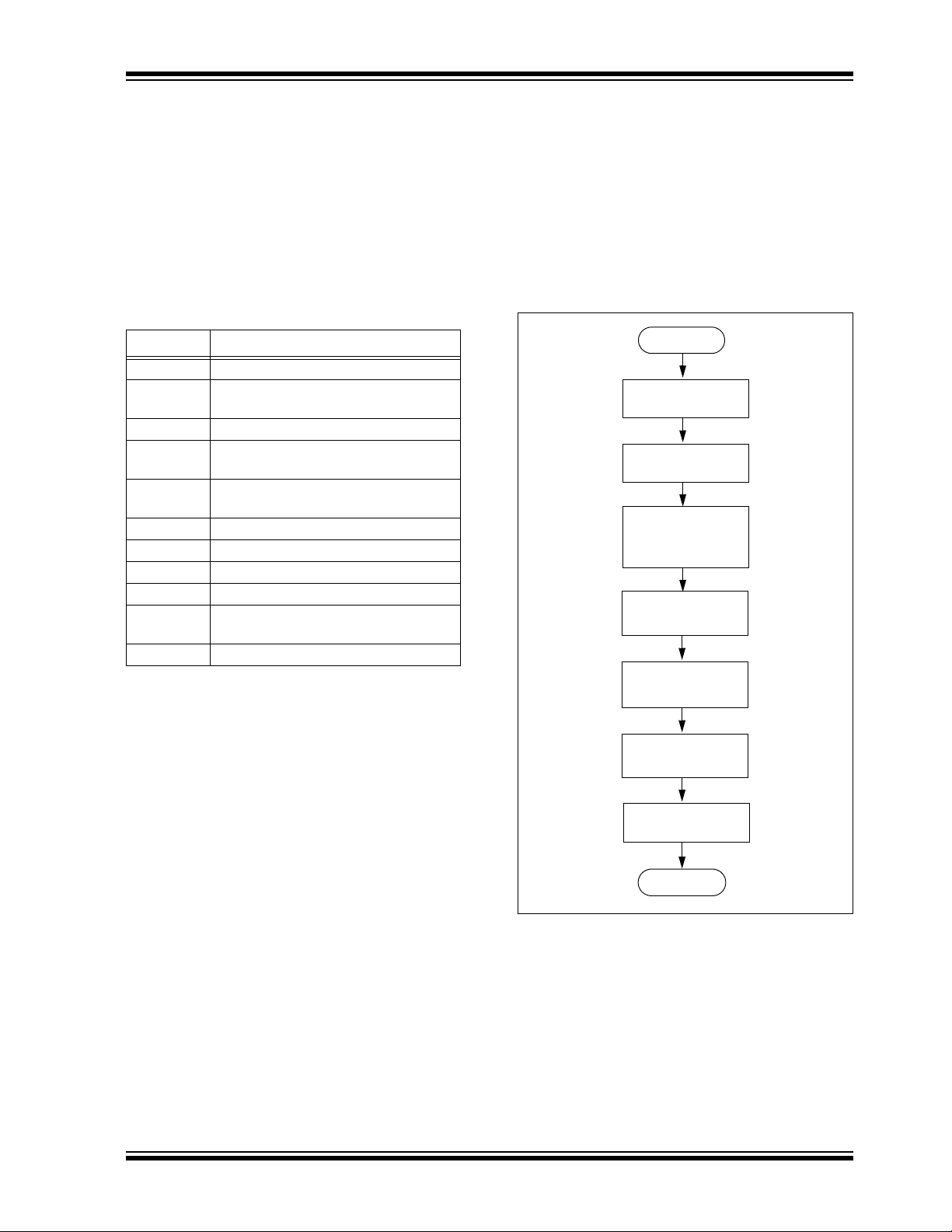
A high-level overview of the programming process is
ill
ustrated in Figure 5-1. The process begins by enter-
ing Enhanced ICSP mode. The chip is then bulk
erased
, which clears all memory to ‘1’ and allows the
device to be programmed. The Chip Erase is verified
before programming begins. Next, the code memory,
data Flash and Configuration bits are programmed. As
these memories are programmed, they are each
verified to ensure that programming was successful. If
no errors are detected, the programming is complete
and Enhanced ICSP mode is exited. If any of the
verifications fail, the procedure should be repeated,
starting from the Chip Erase.
If Advanced Security features are enabled, then
in
dividual Segment Erase operations need to be
performed, based on user selections (i.e., based on the
specific needs of the user application). The specific
operations that are used typically depend on the order
in which various segments need to be programmed for
a given application or system.
Section 5.2 “Entering Enhanced ICSP Mode”
through Section 5.8 “Exiting Enhanced ICSP Mode”
describe the programming process in detail.
FIGURE 5-1: PROGRAMMING FLOW
Start
Program and
Program and
Program and verify
Configuration bits
Finish
verify code
verify data
Enter Enhanced
Exit Enhanced ICSP
Mode
Perform Chip
Erase
Program
Configuration
registers to
ICSP™ mode
default value
器件 Datasheet 文档搜索
AiEMA 数据库涵盖高达 72,405,303 个元件的数据手册,每天更新 5,000 多个 PDF 文件






